IT Solution For Modern World
New Age Innovation
Accelerate Your Online
Presence
Our Services
IT Solutions for Edtech
Product And Services
Skill Development
Online Classes
Man Power Handling

CRYPTOVIBE TECHNOLOGIES PRIVATE LIMITED
WELCOME TO FULL - STACK DATA SCIENCE COURSE
CRYPTOVIBE TECHNOLOGIES PRIVATE LIMITED
WELCOME TO FULL - STACK DATA SCIENCE COURSE
CRYPTOVIBE TECHNOLOGIES PRIVATE LIMITED
INDUSTRIAL ORIENTED TRAINING
CRYPTOVIBE TECHNOLOGIES PRIVATE LIMITED
100% JOB ASSISTANCE

CRYPTOVIBE TECHNOLOGIES PRIVATE LIMITED
WELCOME TO FULL STACK WEB DEVELOPMENT COURSE
CRYPTOVIBE TECHNOLOGIES PRIVATE LIMITED
WELCOME TO FULL - STACK DATA SCIENCE COURSE
- All
- Gallery Item

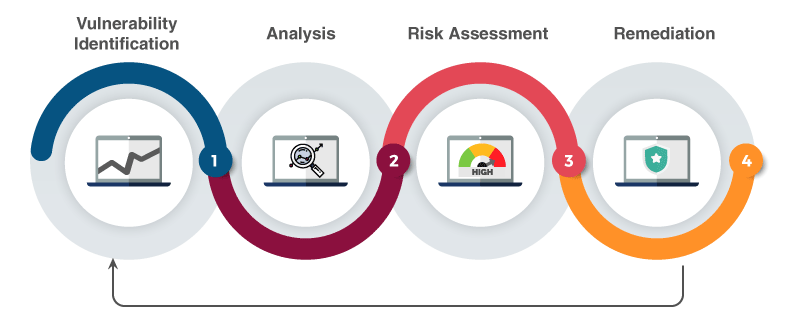
EACH SEMESTER 40 HOURS / LEVEL INCLUDES CYBERSECURITY LABS
CYBER SECURITY COURSE (1 LEVEL)
NETWORK SECURITY ESSENTIAL - BEGINNERS
Network Concepts and Models
What is Networking, Networking Models, OSI Model, TCP/IP, IPv4 and IPv6, WiFi, Security of the Network, Ports and Protocols, Secure Ports
Common Network threats and attacks
Data Center, Cloud Services, Service Models, Deployment Models, MSP, SLA, Network Access Control (NAC), DMZ, VLAN, VPN
network security infrastructure
Spoofing, Phishing, DOS, Virus, Worm, Trojans, On-Path Attack, Side-Channel Attack, Types of Threats, Identify and Preventing Threats, IDS
network security review
Practice the terminology of and review network security concepts
CYBER SECURITY COURSE (2 LEVEL)
NETWORK SECURITY ESSENTIAL - INTERMEDIATE LEVEL
Cyber security foundational concepts
Concepts of cybersecurity principles, information assurance, risk management, terminology, policies, procedures and standards
Cybersecurity controls
Administration controls, physical controls, logical controls, controls review, practices the terminology access controls, review concepts of access control regulation and laws
Incident response, BC and DR concepts
Implementation of Incident Response (IR), Buisness Continuity (BC), and Disaster Recovery (DR) plans, explain how organizations respond to operate during Security Education Training and Awareness (SETA), unplanned disruptions
Network security and security operations
Understanding data security and encryption, controls and asset management, best practice security policies, understand security education recover from and continue security operations
CYBER SECURITY OPERATION - ADVANCE
All the students are engaged with quizes, assignment along with project works
- Address: #72, W.O.C ROAD, MAHALAKSHMIPURA 2ND STAGE BANGALORE 560087
- Hours: Mon-Fri 9:00AM - 5:00PM
- Phone: 9980030616
- Email: info@cryptovibe.in
VISIT US
© 2024 All Rights Reserved.